1. Research Background
Traditional power systems continue to intersect and merge with other energy systems, gradually forming a new ecology of energy interconnection. In the energy Internet, the separation of data usage rights and data ownership, and the separation of information resources and computing resources, highlight the increasingly prominent privacy protection issues in multi-party collaborative optimization. Starting from the typical mode of collaborative optimization in the energy Internet, this paper summarizes the privacy and security risks of traditional third-party proxy computing models and non-third-party interactive computing models. For scenarios involving third parties, a secure proxy computing scheme based on information masking mechanism is proposed. At the same time, for scenarios without third parties, a secure multi-party interactive computing scheme based on the principle of secret sharing is proposed. The proposed schemes, from the perspective of data privacy and computing security, safeguard the rights of data owners, curb and reduce the risk of data leakage in the collaborative optimization of energy Internet, and achieve reliable privacy protection.
2. Research Content
2.1 Privacy Risks of Multi-party Collaborative Optimization
In the two typical modes of collaborative computing, the third-party agent computing mode completes tasks through centralized computing after aggregating information, showing the characteristics of "information centralization and computation centralization"; while the interactive computing without a third party does not require information aggregation, and the participating parties retain their privacy information, and complete the calculation through necessary information interaction with other subjects, showing the characteristics of "information dispersion and computation dispersion". Even though the two modes of computing with and without a third party have differences in the organization of computing and information resources, they both unavoidably involve real information interaction.
A feasible approach to privacy protection is to privatize the "out-of-domain" data, so that the real data in the trusted domain is transformed into privacy attribute-free confidential data through desensitization, confusion, encryption, etc. before entering the non-trusted domain, thereby achieving reliable privacy protection of the "out-of-domain" data. Although transforming the real data from the "out-of-domain" into confidential data can reliably protect information privacy, how to carry out collaborative computing based on confidential data becomes a new problem for all parties. Therefore, the privacy protection solution for multi-party collaborative computing in the energy internet essentially needs to solve the problem of joint computing on confidential data.
Selecting suitable algorithms and frameworks to complete the privacy configuration of computing resources and information resources is the key to achieving privacy protection in collaborative computing in power systems. Privacy-aware multi-party collaborative computing solutions can be designed from the five dimensions of "data, subject, model, algorithm, framework".
2.2 Security Agent Computing Based on Information Disguise Mechanism
The security agent computing scheme based on information disguise is aimed at the presence of a third party, as shown in Figure 1. In the context of the energy internet, the cloud energy management system (EMS) services that use cloud services as third-party computing resources are very compatible with this privacy protection solution. The core feature of secure agent computing is that the third party obtains confidential data from participating subjects and completes privacy computation.
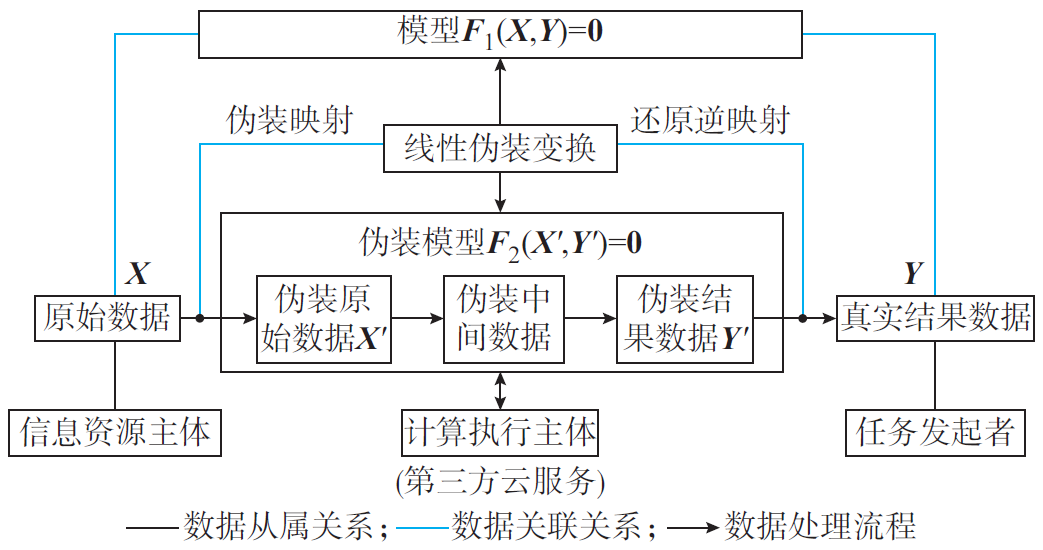
Figure 1: Secure proxy computing based on information camouflage
To ensure that the cloud cannot obtain real information, local participants use information disguise techniques based on linear mapping to design special operators to transform real information into disguised information. The cloud completes the computation based on the disguised information and delivers the result to the local entity. Locally, by using information disguise operators to reverse the disguised result and obtain the real result. This privacy protection scheme is suitable for energy management scenarios involving multiple entities in the energy internet, such as building EMS, home EMS, electric vehicle cluster EMS, multi-energy microgrid EMS, etc.
2.3 Secure Multi-party Interactive Computing Based on the Secret Sharing Principle
The secure interactive computing scheme based on the secret sharing principle is aimed at situations without a third party, as shown in Figure 2. This scheme is based on secure multiparty computing technology, and has the characteristics of strong generality and high security, and is suitable for establishing a universal multi-party privacy computing architecture. The core feature of secure multiparty computing is that multiple computing nodes obtain confidential data from participating subjects and complete privacy computation.
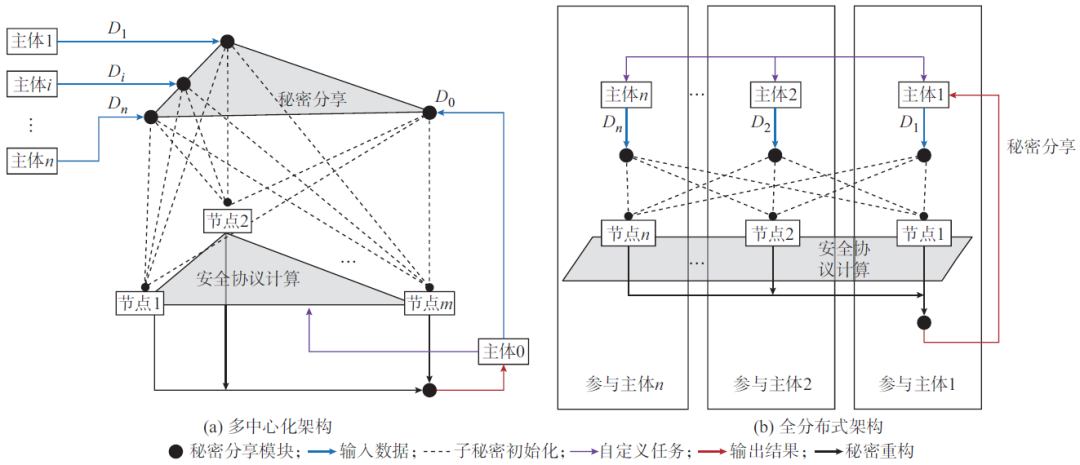
Figure 2: Two SMPC architectures based on secret sharing
According to the number of participating entities and computing nodes, different computing architectures can be used for secure multiparty computing. If a computing node is deployed at each participating entity, it constitutes a fully distributed computing architecture. This architecture is suitable for collaborative optimization scenarios between large energy systems in the energy internet, such as the coordinated optimization and scheduling of power-natural gas and power-heat coupled systems. If a few participating entities deploy computing nodes as representatives, it constitutes a multi-center computing architecture. This architecture has platform characteristics and is suitable for distributed trading scenarios involving a large number of entities in the energy internet, and so on.
3. Conclusion
When privacy computing technology is applied to the power system, on the one hand, it is necessary to ensure that the relevant privacy processing does not affect the accuracy of task computation results while enhancing the strength of data privacy protection. On the other hand, attention needs to be paid to the application costs of different technical routes. Privacy computing solutions need to minimize the complexity of computation and communication as much as possible, and adapt to the requirements of different scenarios in terms of real-time performance, and so on. This is a major bottleneck in the application of current privacy computing technology to complex industrial collaborative tasks. The intersection and integration of the field of privacy computing with the field of power systems in terms of theoretical research and practical application require analysis from both perspectives. From the perspective of privacy computing, mature technical directions that have accumulated in fields such as computer science provide tools with a reliable theoretical foundation for power system researchers to conduct privacy protection research. From the perspective of power systems, the differences in the characteristics of actual computing tasks in physical scenarios and mathematical models determine that the design of a privacy protection scheme needs to be targeted. Addressing the privacy protection requirements in specific scenarios, starting from the information interaction link, model coupling link, and combining the characteristics of privacy computing technology with the characteristics of actual task scenarios, to design privacy protection solutions that meet application requirements.
Reference
GUO Qinglai, TIAN Nianfeng, SUN Hongbin. Key Technologies of Privacy Computation Supporting Collaborative Optimization of Energy Internet[J]. Automation of Electric Power Systems, 2023, 47(8):2-14.
Extended Reading
XIN S, GUO Q, WANG J, et al. Information masking theory for data protection in future cloud-based energy management[J]. IEEE Transactions on Smart Grid, 2017, 9(6): 5664-5676.
TIAN N, DING T, YANG Y, et al. Confidentiality preservation in user-side integrated energy system management for cloud computing[J]. Applied Energy, 2018, 231: 1230-1245.
TIAN N, GUO Q, SUN H. Privacy preservation method for MIQP-based energy management problem: a cloud-edge framework[J]. Electric Power Systems Research, 2021, 190: 106850.
TIAN N, GUO Q, SUN H, et al. Fully privacy-preserving distributed optimization in power systems based on secret sharing[J]. iEnergy, 2022, 1(3): 351-362.
About the Authors

Guo Qinglai is a communication author, professor, and doctoral supervisor. His main research direction is energy management, voltage control, and cyber-physical systems. E-mail: guoqinglai@tsinghua.edu.cn.

Tian Nianfeng is a doctoral student, his main research direction is power system optimization scheduling considering privacy protection. E-mail: tnf18@mails.tsinghua.edu.cn.

Sun Hongbin is a professor and doctoral supervisor, focusing on research areas such as energy internet, smart grids, and the operation and control of power systems. E-mail: shb@tsinghua.edu.cn